Password Security
It's common knowledge that every passing year, our computers get faster and more powerful, yet we still keep our passwords the same as they were the year before and never tend to worry about the effect this has on our security.
In this guide we're going to explain to you the importance of using a strong password, how to create one and how to make it as difficult as you can for hackers to break into your account.
Is your password good or bad?
What is a bad password?
A bad password can be determined in many ways, but for the purpose of this guide we will describe it as any password that takes under 1 week to crack using conventional dictionary or brute force methods from an average modern day desktop computer.
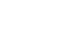
When creating a password, many people don’t take into consideration the strength of their password and focus entirely on creating a password that they can remember, often leading to passwords like the ones seen below:
123456
123456789
12345
Qwerty
Password1
These passwords are among the most common passwords used at the time of writing this guide, and can all be hacked in under a second due to them being easy targets for both dictionary and brute force attacks.
Most often, people will try to create a password that includes information that's memorable to them but mix it up by adding some numbers at the end and a capital letter at the start. The example below contains other commonly cracked password that people still tend to use.
Jamie1997 - This password uses the person's name along with his date of birth, if this was a targeted attack, the hacker could manage to guess this from information provided by social media. However, if the hacker decided to use any of the methods mentioned later on in this guide the password would take around 16 hours to break.
What makes the above password insecure isn't necessarily it's complexity but instead its likeliness to be used. Using any name or significant date that can be found on your social media whether it's yours, a relative's or a pets reduces the passwords strength and makes the hackers job a lot easier.
What is a good password?
A strong password, is a password that cannot be cracked in a reasonable amount of time. For the purpose of this guide we will consider that length of time 1 year from an average desktop computer. When designing a strong password, it is essential to take into consideration the tactics and tricks hackers will use to try and break it, these are listed below along with their examples.

Allow us to help you manage your digital security.
Need help with your password? Contact Us NowDictionary attacks
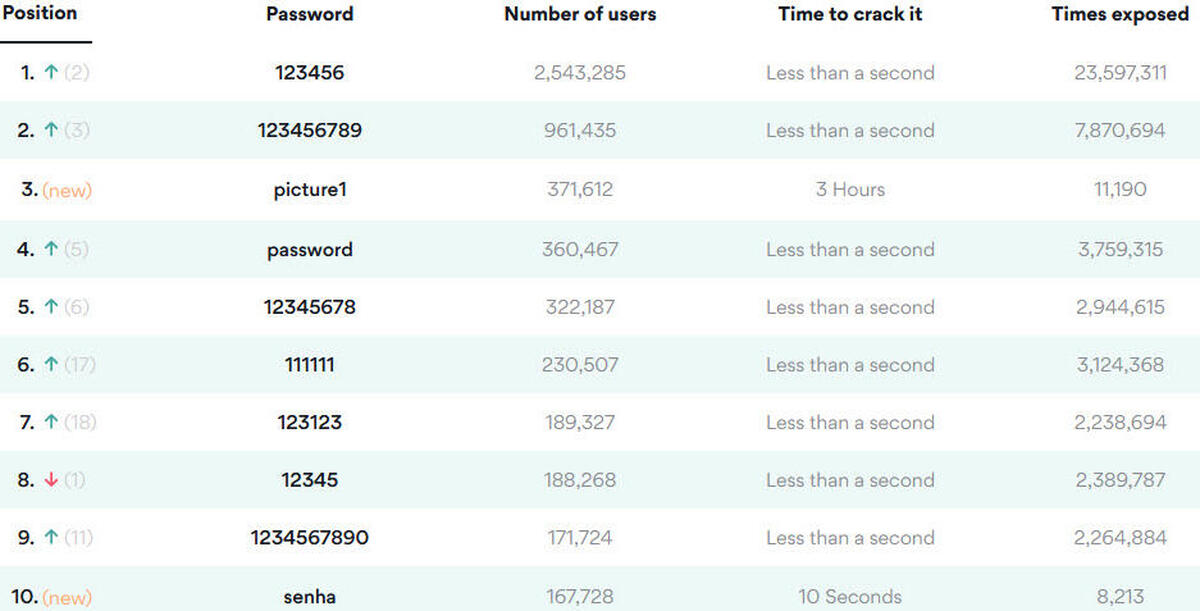
A dictionary attack is a technique where attackers attempt to use common words and phrases loaded in from a massive database to guess passwords. The fact people often use simple passwords across multiple accounts means dictionary attacks can be successful while requiring fewer resources to execute.
For example, the largest password dictionary available on the internet (Known as "rock you 2021") Contains over 32 million commonly used word and phrase combinations that people use in passwords, these include the following:
Finland2020
$4turd4y
3min3m
Candlestick1
Password
P4ssw4rd
Passw0rd1
As you can see above, a dictionary attack doesn't just use the actual word, but also use as many possible variants of that word that it can use to increase the chance of success. This means that passwords like the ones above have a higher susceptibility to dictionary attacks than they do to brute force attacks.
Brute force attacks
While all of the attacks under this list fall under the umbrella term of "Brute force attacks" When referring to a brute force attack we often mean the attack is using slow trial and error methods to crack passwords, for example:
AAAAAAA < Computer is given a certain amount of letters and numbers to try and guess
AAAAAAB < Computer begins to try every letter and number in a sequence
AAAAAAC
…
AAAAABA < Once it has hit Z on the last character, it will try the numbers 1-9 and then special characters before populating the next column
…
XdFK4ma < This proccess repeats its self until the password is cracked
Combination attacks
A combination attack is a mixture of both a dictionary attack and a brute force attack. These are most commonly used when the hacker is targeting one person or a specific organisation that they have already gathered information on.
These attacks are usually bespoke and created entirely based around a list of information that has been gathered and then the brute force attack is used to create variants, for example:
If the hacker has spotted that you used you used the password "hammer12" in a previous password, they may connect this to a program that attempts a sequence of variants such as:
Hammer01
Hammer02
Hammer03
…
Hammer2021
The hacker does not necessarily need your previous password to achieve this, for people with large digital footprints, all of the information they require could be found via your social media. So the hacker can take details such as your name, pets name, your age, children's birthdays ETC and combine them into one attack that tries millions of different variants.
recallability
After reading all of the information above it may spring to mind that the best passwords to create are randomly generated combinations such as "Cfk;392!'d@-2123r" and you wouldn't be wrong, this password would take an estimated 9 billion years to crack from a standard desktop computer!
However this password isn't very convenient to remember, so we can compromise on the security a bit to create a password that can be remembered much more easily, while still be able to hold up against all types of attack mentioned in this guide.
If you are familiar with the "What 3 words app", you may know that there are 57 trillion different combinations you can make from three any three random words, you can then add extra security steps into them such as capital letters in the words and a number at the end.
This means that a password such as "CookedFreakyTelevision4819" will still take an estimated 297 years to crack while still being easy to memorise.
Need help securing your data?
Contact Us NowExtra steps you can take.
Be careful where you put it!
One of the easiest ways a hacker can get your login details is by obtaining databases from websites that are outdated, insecure or just badly built. Others prefer to use scam emails and phishing websites to trick you into handing over your password voluntarily. Be sure to check out our guide on spotting scam emails found here: Phishing emails - Red Dune IT

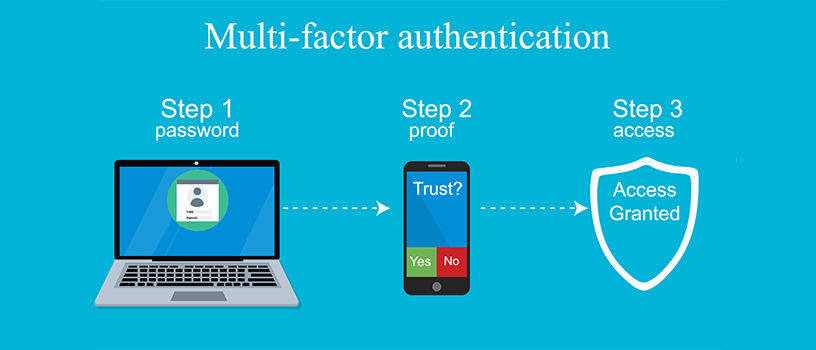
Multifactor Authentication (MFA) and Two Factor Authentication (2FA)
Enabling Multi-Factor Authentication / 2Factor Authentication on all of your accounts is by far the safest way to mitigate a hacking attempt. Almost all major software platforms support this and it's easy to switch on.
Different passwords
While it can be a pain to use different passwords for different services, we recommend at least having the password for your primary email set to be something completely different from the rest. This is because your email can be considered the holy grail to a hacker as it can be used to reset the passwords of all other accounts that are registered to it.

Password managers
Password managers take away the annoyance of having to memorise all of your passwords by storing them for you. This means that via the use of one strong master password you can access of the others, and even autofill them into the password box.

Allow us to help you manage your digital security.
"Red Dune IT Solutions are a top notch company and I would highly recommend them."
- Anne Becket-Allen, Rosedale Funeral Home
"Speaking to my neighbours who require a new home computer system, the reaction I got was where to go? The dealer in Wymondham has gone as has the one in Long Stratton. Yes, you can purchase blind from the likes of PC world etc. But should you require advice and support then I would recommend for anyone in the south Norfolk area to contact Red Dune computer systems 01986888274 who will visit at home or business, quote, install, train and provide backup and support. In my opinion a company that does what it says it will!. To confirm, I have no financial interest in Red Dune, just a satisfied customer."
- Peter Holden